We have run a successful schools’ coding program for several years. Introducing primary age children to Sony as a company as well as Raspberry pi computers. However, we had not yet developed a program specifically for secondary age students. This was something we wanted to change for this year.
As we spend more time working and schooling online, it is essential for pupils to have a greater understanding of cyber security and the associated threats. Many schools do not focus on cyber security explicitly as part of their computing curriculum. Even at degree level, 39 percent of UK Computer Science degree courses do not offer mandatory cyber security content (Ruiz, 2019). Only 17 percent of courses offer cyber security content in the first year. We felt that cybersecurity should be the focus of our workshop.
The Raspberry Pi Foundation develop many high quality resources and their projects focusing on cryptography and ethical hacking are an ideal to introduction to these elements of cybersecurity. This post will provide an overview of the workshop.
The first activity introduces students to the concept of a cipher. A type of secret code, where letters are swapped to encrypt (hide) the message. The oldest, and one of the most famous ciphers is the Caesar cipher, as used by Julius Caesar around 58 BC. Here, the alphabet is written in a circle.
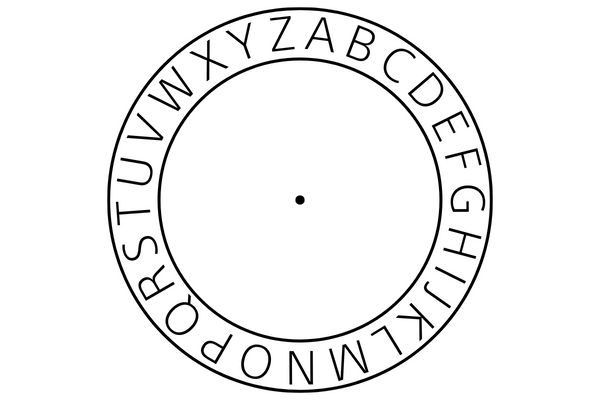
To make a secret encrypted letter from a normal one, you use a secret key. This can be any number, for example 5. The normal letter is substituted for the letter that is 5 letters clockwise in the circle. The key is then repeated for each word in the message. The person receiving the message then uses the reverse key (in this case, 5 letters anti-clockwise) to decrypt the message. We will do this activity first on paper before using Python to create a program that will encrypt and decrypt messages.
We will then discuss the limitations of a secret key. These messages can be decrypted by someone trying every number between 1 and 26 as a key to see which ones make sense or looking at two or three letter words in the message and use these to work out the key.
In our next activity we will create messages that are unbreakable using an encryption technique called a one-time pad.
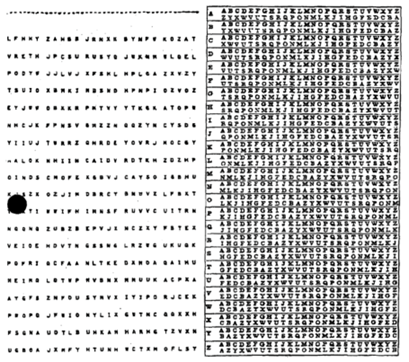
We begin by creating the one-time pad in Python, which is a random secret key, as opposed to a single numerical key. The one-time pad is then used within a program to encrypt and decrypt messages inputted by the user.
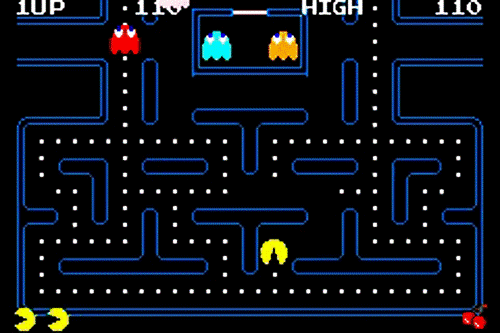
The final activity will introduce students to the concept of ethical hacking. We will infect our Raspberry Pi computers with (pretend) viruses and then navigate the terminal attempting to quarantine and remove them. This will take the form of a Pac Man style game.
Each virus is named after a Pac Man ghost and on opening the quarantined virus, students can calculate their score. There may be prizes for the winners!
We will be piloting the workshop at the end of this month and my next post will reflect on how it went.
The projects that we will be using are available here.
by Steve Lewis @Steve_Lewis81
Ruiz, N. (2019). A Study of the UK undergraduate Computer Science Curriculum: A Vision of Cybersecurity. 2019 IEEE 12th International Conference on Global Security, Safety and Sustainability (ICGS3), (1-8)
How can we help?
If you are looking for a Contract Electronics Manufacturing partner, submit your enquiry today and a member of our team will be in touch shortly.
Are you experiencing an issue with your Sony product? Tell us about it and our team of expert technicians will be in touch.
Are you looking for office space with fantastic amenities and 24/7 security? Enquire today with your requirements and our team will be in touch with information about our availability.
We are a socially aware business which seeks to support our local community You can submit your request today using the form on the right. Please note that we can only support requests within a 30 mile radius from our facility. Our committee reviews requests on a monthly basis, so please allow a few weeks for our team to respond.
To arrange a visit for your school as a part of our educational programs, please submit your inquiry today. Our committed team will respond with guidance regarding availability within a week.
Ready to join the Sony team? Please submit your CV and cover letter today using the form on the right and our recruitment team will be in touch.
